When it comes to IT in healthcare, the HIMSS conference is the gold standard for healthcare trade shows. This year, HIMSS16 will be held February 29- March 4 in Las Vegas at the Sands Expo and Convention Center, and will be hosting over 40,000 attendees, including clinicians, speakers, and vendors. HIMSS16 boasts more than 300 educational programs and will showcase cutting-edge technology available to the healthcare sector. NCS Technologies will be at HIMSS16, and will have experts ready to discuss all IT healthcare security concerns at Booth #11118.
Katie Callahan
Recent Posts
Deployable Virtual Desktop Infrastructure Solutions
Posted by Katie Callahan on Feb 4, 2016 3:49:06 PM
When the need arises, war fighters, first responders and industry may leverage existing organizational VDI infrastructure and expertise to meet any challenge, anywhere. NCS Technologies allows for the rapid deployment of IT infrastructure into the field without the weight and footprint of traditional solutions. NCS offers hyper-converged back-end solutions and end points intelligently integrated into rugged transit cases. These cases are capable of supporting large numbers of clients in the field without losing centralized control while simultaneously delivering ease of maintenance. This approach also simplifies the IT aspects of the reset process that must occur upon returning from deployments. Our three solutions are:
Topics: VDI
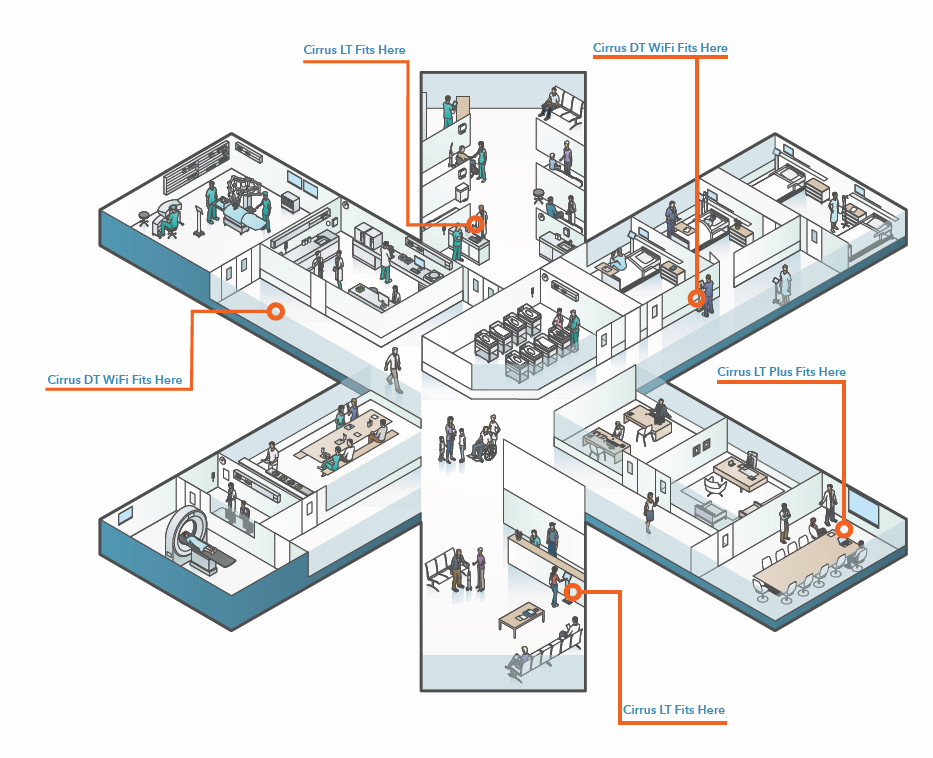
IT administrators in healthcare tell us they are are focused on making computing more secure, more reliable, less complex and more cost effective - goals that make sense to everyone.
Healthcare workers rely on computers and networking in nearly every aspect of their jobs. Patient records and scheduling need to be kept up to date and secure. Imagery such as MRIs and X-rays need to be available and accessed from distant servers. Doctors and nurses are constantly on the move and frequently use carts to bring mobile computing - and the latest patient information - directly into each patient area.
Topics: VDI, Healthcare
Organizations look to implement desktop or end point virtualization for many reasons, including enhanced security, lowering costs, reducing IT complexity - even lowering energy consumption. Virtualized end points are particularly effective in meeting these objectives as infrastructure management and data are centralized in the data center.
Virtual Desktop Infrastructure (VDI) implementation continues to grow, but many IT managers and users still have limited experience with the technology - mostly as an immobile desktop implementation consisting of a monitor, keyboard, mouse and small desktop networking device. This description fits both thin and zero clients. In fact, thin and zero client devices may look identical. But do not be fooled!
Topics: VDI
Virtual PCoIP PC Strong Defense Against Cyber Attacks
Posted by Katie Callahan on May 29, 2015 10:20:39 AM
This spring, the Department of Defense announced their new cyber protection strategy, which ultimately aims to prevent cyberattacks by nation-states and hacker groups alike. The DoD emphasized the need to strengthen both its cyber defense and cyber deterrence posture in order to best protect against cyberattacks of potentially significant consequence.
Although nation-states, particularly China and Russia, are adept at exploiting holes in security, equally worrisome threats come from hacker organizations affiliated with terror groups or gangs who perpetrate criminal cyberattacks for profit. Hackers of all stripes never rest in seeking out security vulnerabilities, while IT departments remain on a continuous treadmill of cyber defense, updates and patches. IT managers realize their networks remain vulnerable at the weakest spot in the perimeter, often a desktop lagging behind on security updates, or an operating system breached because of an exposure to a zero-day vulnerability. This constant grind leaves cyber security forces overworked and exhausted.
VDI, A Strong Addition to Your IT Security Strategy
Cyberattacks and data breaches are a ubiquitous problem in today’s data-driven world, and often result in dire consequences for the compromised party and the IT organization as a whole. For the government and commercial sector, the threat only seems to grow. For instance, in the government sector, the rate of cyberattacks is on the rise. Between 2010 and 2013, attacks on government agencies rose 35%.
Topics: VDI