Mike Turicchi
Recent Posts
Apple silicon: Power, Security, and Sustainability for Business Success
Posted by Mike Turicchi on Dec 9, 2024 2:26:48 PM
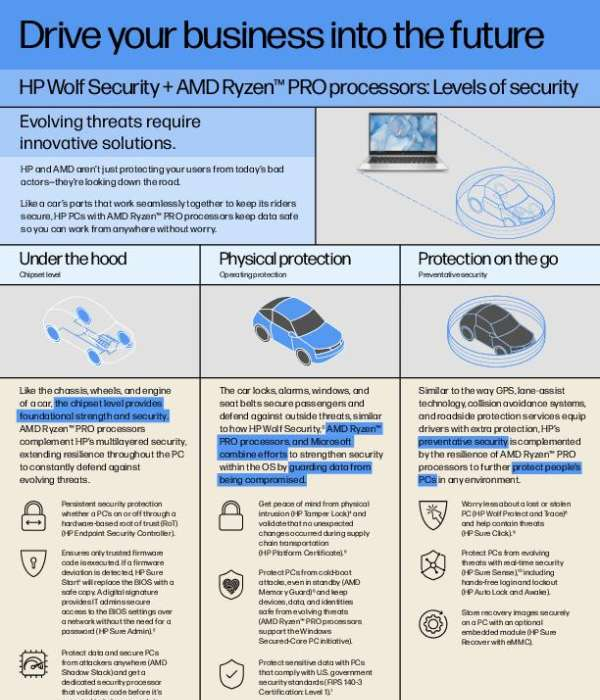
Drive your business into the future. HP Wolf Security + AMD Ryzen™ PRO processors: Levels of security
Posted by Mike Turicchi on Dec 9, 2024 11:23:10 AM
Empower the Do-Everything, From-Anywhere Workforce
Posted by Mike Turicchi on Dec 2, 2024 2:23:08 PM
Empower the Do-Everything, From-Anywhere Workforce
Posted by Mike Turicchi on Nov 26, 2024 11:10:18 AM
How to Put AI Models into Production: A Guide to Accelerated Inference
Posted by Mike Turicchi on Nov 25, 2024 4:11:32 PM
NVIDIA AI Workbench: Develop, collaborate on, and accelerate AI and machine learning workflows - from anywhere
Posted by Mike Turicchi on Nov 19, 2024 2:12:52 PM
The Future of AI PCs: How Mac is Leading the Charge
Posted by Mike Turicchi on Nov 19, 2024 9:11:56 AM
Keeping it Together: Overcoming Today's PC Management Challenges
Posted by Mike Turicchi on Nov 18, 2024 2:20:45 PM