Mike Turicchi
Recent Posts
Microsoft Defender for Office 365 Receives Highest Award in SE Labs Enterprise Email Security Services Test
Posted by Mike Turicchi on Jul 31, 2023 12:33:48 PM
Protecting School Districts with Threat Containment
Posted by Mike Turicchi on Jul 31, 2023 10:33:01 AM
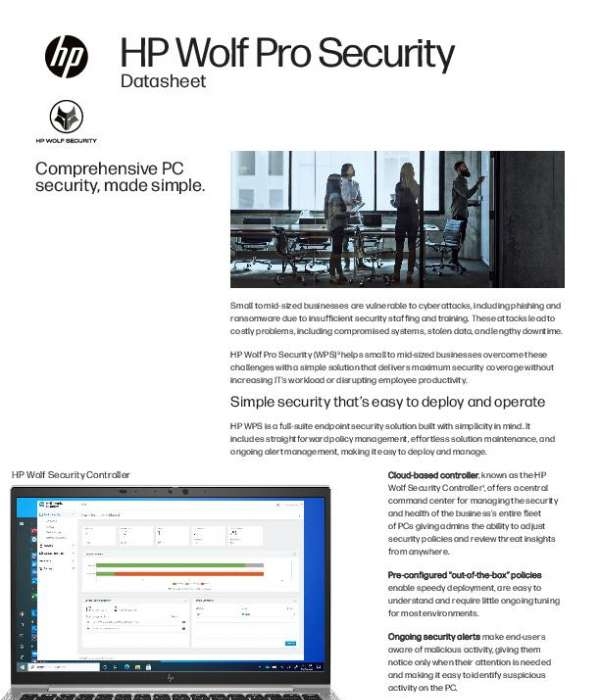
HP Wolf Pro Security: Comprehensive PC security, made simple
Posted by Mike Turicchi on Jul 24, 2023 5:27:14 PM
Wolf Pro Security for Small and Mid-Sized Organizations
Posted by Mike Turicchi on Jul 24, 2023 10:31:44 AM
Test your team's security readiness with the Gone Phishing Tournament
Posted by Mike Turicchi on Jul 17, 2023 12:36:37 PM
HP Wolf Pro Security: Comprehensive PC security, made simple
Posted by Mike Turicchi on Jul 17, 2023 10:33:09 AM
Announcing Availability: Ryzen 7045 HX Series Processors
Posted by Mike Turicchi on Jul 10, 2023 5:30:14 PM